TikTok Sued by US Government, Dark Angels Receives Record-Breaking $75M Demand: Your Cybersecurity Roundup

TikTok Sued by US Government, Dark Angels Receives Record-Breaking $75M Demand: Your Cybersecurity Roundup TikTok Sued by US Government for Violating Children’s Privacy TikTok is facing a lawsuit from the US Department of Justice and the Federal Trade Commission for violating children’s privacy laws. The lawsuit alleges that TikTok knowingly allowed children to create accounts […]
How to Decrypt Hashes

How To Decrypt Hashes Introduction Hashes.com is a robust platform widely employed in penetration testing. Offering a suite of tools, including hash identifiers, hash verifier, and base64 encoder and decoder, it’s particularly adept at decrypting popular hash types like MD5 and SHA-1. In this article, we’ll delve into the practical process of decrypting hashes using […]
Vulnerability Management as a Service: The Smart Way to Protect Your Organization

Vulnerability Management as a Service: The Smart Way to Protect Your Organization What is Vulnerability Management? With all the coding and software companies use, there’s always security vulnerabilities. There can be code at risk and a need to secure applications. That’s why we need to have vulnerability management. But, we already have so much on […]
Vulnerability Management as a Service: The Key to Compliance

Vulnerability Management as a Service: The Key to Compliance What is Vulnerability Management? With all the coding and software companies use, there’s always security vulnerabilities. There can be code at risk and a need to secure applications. That’s why we need to have vulnerability management. But, we already have so much on our plate to […]
How Vulnerability Management as a Service Can Help You Save Time and Money

How Vulnerability Management as a Service Can Help You Save Time and Money What is Vulnerability Management? With all the coding and software companies use, there’s always security vulnerabilities. There can be code at risk and a need to secure applications. That’s why we need to have vulnerability management. But, we already have so much […]
5 Benefits of Vulnerability Management as a Service
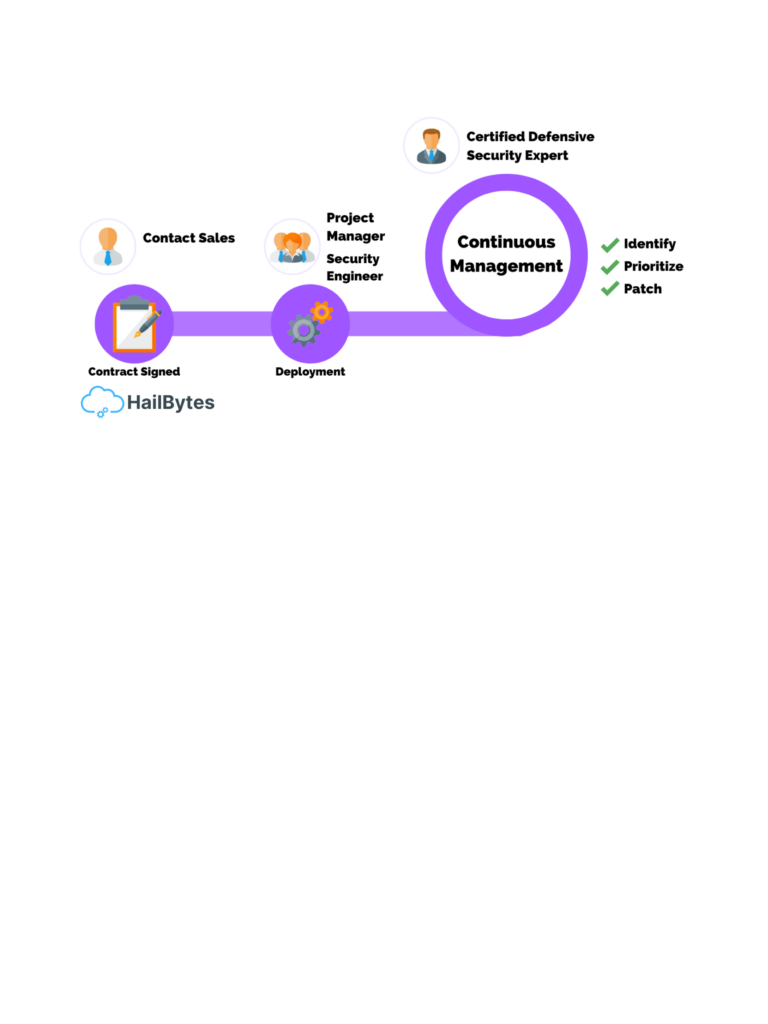
5 Benefits of Vulnerability Management as a Service What is Vulnerability Management? With all the coding and software companies use, there’s always security vulnerabilities. There can be code at risk and a need to secure applications. That’s why we need to have vulnerability management. But, we already have so much on our plate to worry […]
