There are several helpful open source alternatives in addition to the native security solutions that cloud companies supply.
Here’s an example of eight outstanding open source cloud security technologies.
AWS, Microsoft, and Google are just a few cloud companies that provide a variety of native security features. Although these technologies are undoubtedly helpful, they cannot satisfy everyone’s needs. IT teams frequently discover gaps in their capacity to safely create and maintain workloads on all these platforms as cloud development progresses. In the end, it’s up to the user to close these gaps. Open source cloud security technologies are useful in situations like this.

Widely used open source cloud security technologies are frequently created by organizations like Netflix, Capital One, and Lyft that have sizable IT teams with substantial cloud expertise. Teams start these projects to solve certain requirements that aren’t being met by the tools and services that are already available, and they open source such software in the hope that it will be useful to other businesses as well. Although it’s not all-inclusive, this list of the most well-liked open source cloud security solutions on GitHub is an excellent place to start. Many of them are compatible with other cloud settings, while others are built expressly to function with AWS, the most popular public cloud. Look at these security technologies for incident response, proactive testing, and visibility.
Cloud Custodian
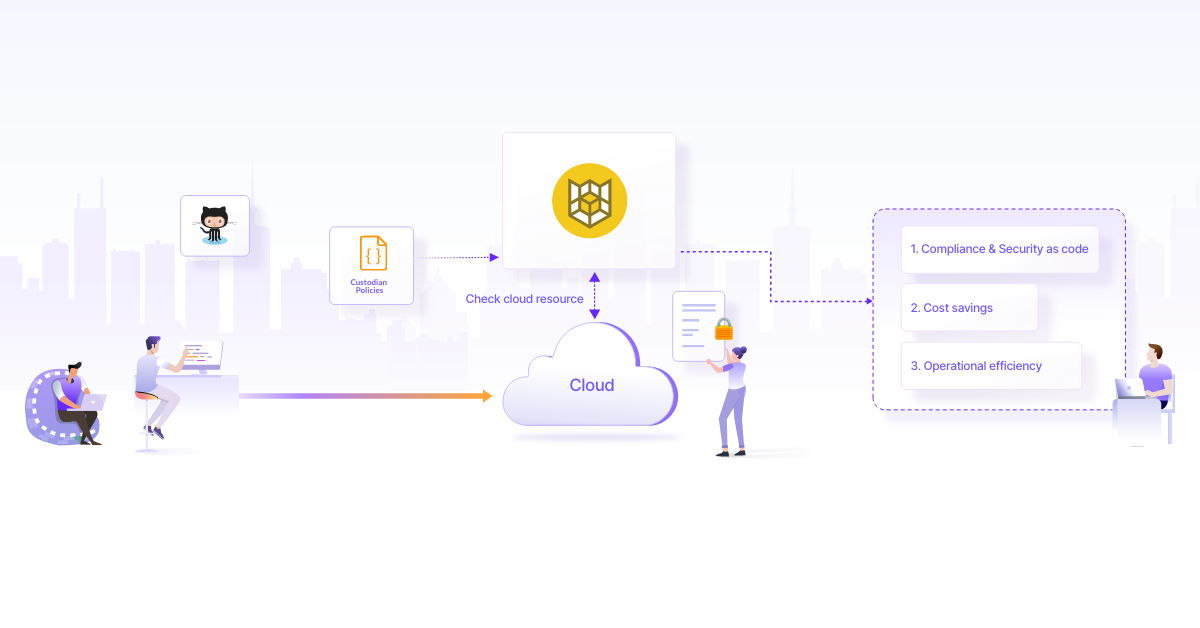
The management of AWS, Microsoft Azure, and Google Cloud Platform (GCP) environments is done with the help of Cloud Custodian, a stateless rules engine. With consolidated reporting and analytics, it combines several of the compliance routines that enterprises employ into a single platform. You may establish rules using Cloud Custodian that compare the environment to security and compliance requirements as well as criteria for cost optimization. The kind and group of resources to check, as well as the actions to be taken on these resources, are expressed in Cloud Custodian policies, which are defined in YAML. You may, for instance, establish a policy that makes bucket encryption available for all Amazon S3 buckets. To automatically resolve rules, you may integrate Cloud Custodian with serverless runtimes and native cloud services. Initially created and made available as free source by
Cartography
The main draw here is the Infrastructure maps that are made by cartography. This automatic graphing tool provides a visual representation of the connections between your cloud infrastructure components. This can increase the team’s overall security visibility. Utilize this tool to create asset reports, identify potential attack vectors, and pinpoint security improvement opportunities. Engineers at Lyft created cartography, which utilizes a Neo4j database. It supports a variety of AWS, G Suite, and Google Cloud Platform services.
Diffy
A highly popular tool triage tool for digital forensics and incident response is called Diffy (DFIR). Your DFIR team’s responsibility is to search your assets for any evidence the intruder left behind after your environment has already been attacked or hacked. This may require painstaking hand labor. A differencing engine offered by Diffy reveals anomalous instances, virtual machines, and other resource activity. In order to help the DFIR team pinpoint the locations of attackers, Diffy will inform them of which resources are acting oddly. Diffy is still in its early stages of development and now only supports Linux instances on AWS, however its plugin architecture could enable other clouds. The Security Intelligence and Response Team of Netflix invented Diffy, which is written in Python.
Git-secrets
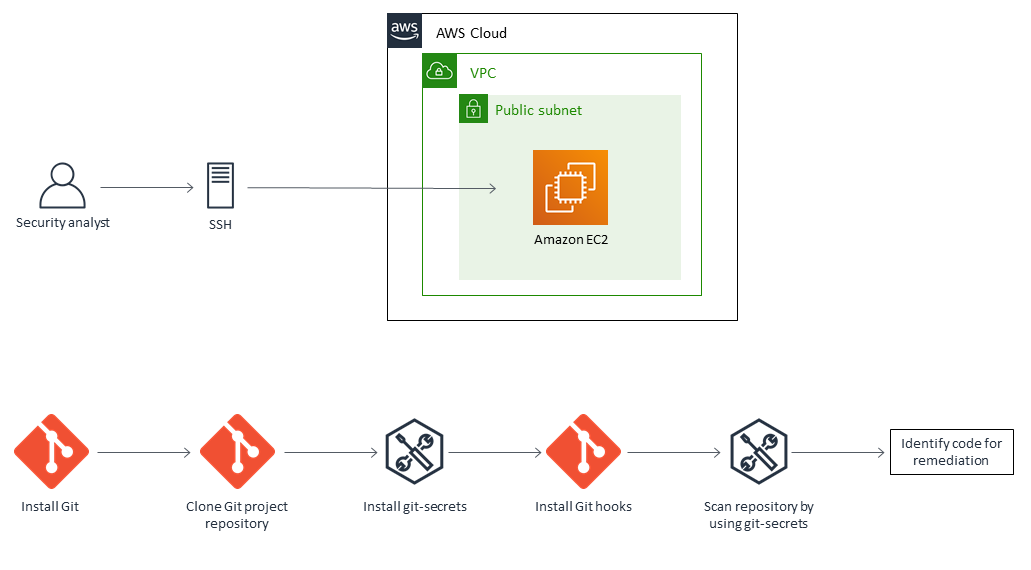
This development security tool called Git-secrets forbids you from storing secrets as well as other sensitive data in your Git repository. Any commits or commit messages that fit one of your predefined, forbidden expressions patterns are rejected after being scanned. Git-secrets was created with AWS in mind. It was developed by AWS Labs, which is still responsible for project maintenance.
OSSEC
OSSEC is a security platform that integrates log monitoring, security information and event management, and host-based intrusion detection. You may use this on cloud-based VMs even though it was originally designed for on-premises protection. Platform’s adaptability is one of its advantages. Environments on AWS, Azure, and GCP may use it. Additionally, it supports a variety of OSes, including Windows, Linux, Mac OS X, and Solaris. In addition to agent and agentless monitoring, OSSEC offers a centralized administration server for keeping track of rules across several platforms. OSSEC’s salient characteristics include: Any file or directory change on your system will be detected by file integrity monitoring, which will notify you. Log monitoring gathers, examines, and notifies you to any unusual behavior from all of the logs in the system.
Rootkit detection, which alerts you if your system undergoes a change like a rootkit. When particular intrusions are discovered, OSSEC may respond actively and act right away. The OSSEC Foundation oversees the upkeep of OSSEC.
GoPhish
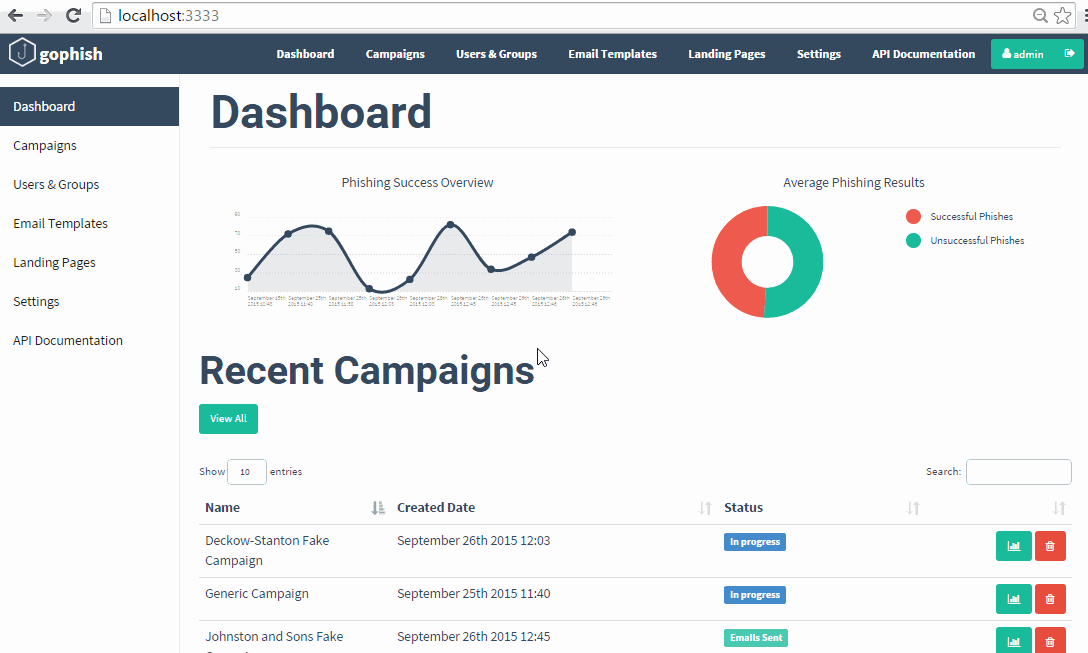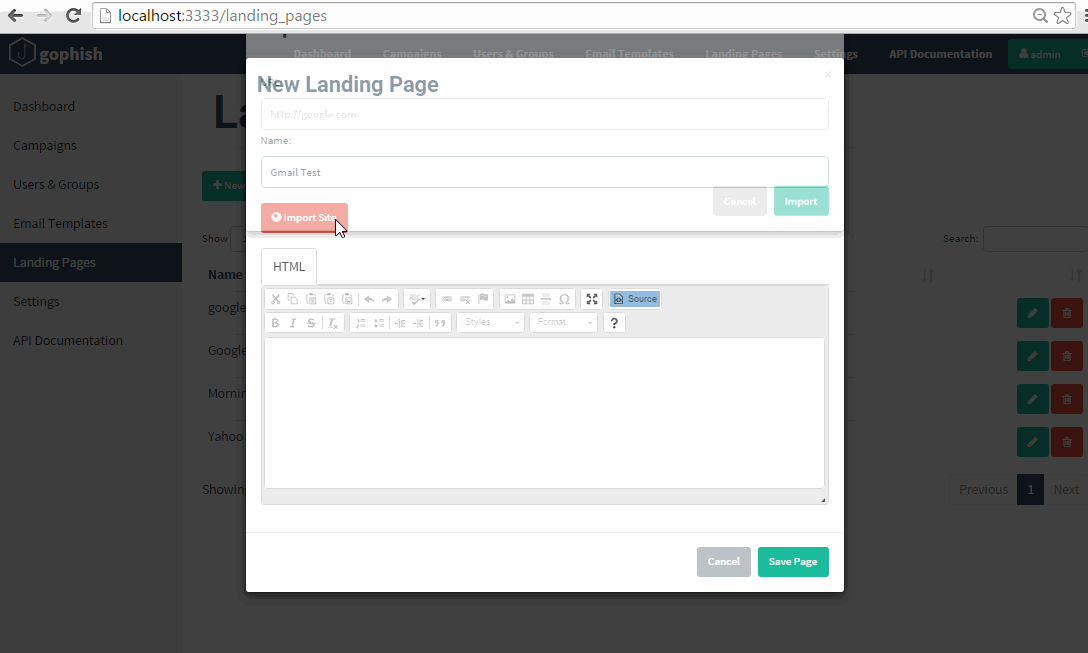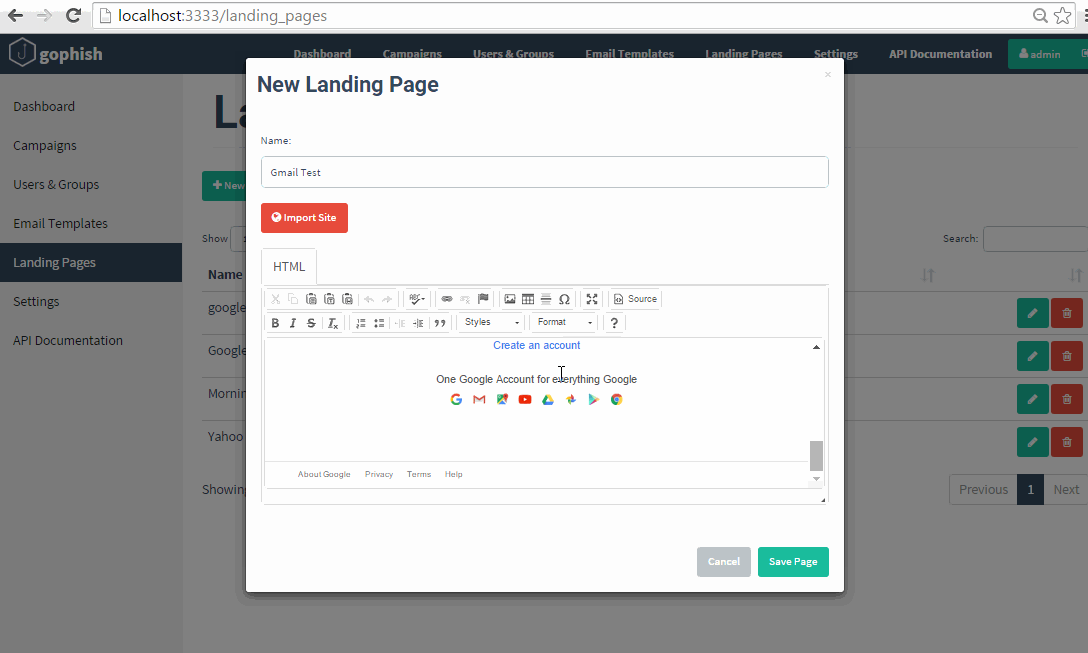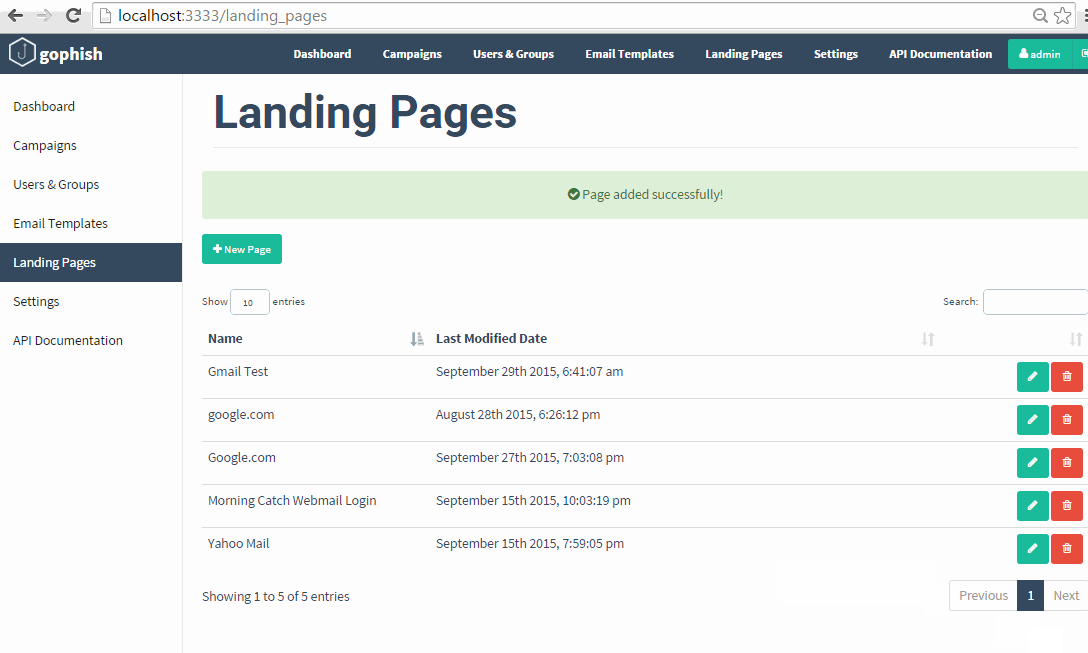
For phish simulation testing, Gophish is an open-source program that enables sending emails, tracking them, and determining how many recipients clicked links in your phony emails. And you can look up all of their statistics. It gives a red team a number of attack methods including regular emails, emails with attachments, and even RubberDuckies to test physical and digital security. Currently over 36 phishing templates are available from the community. An AWS-based distribution pre-loaded with templates and secured to CIS standards is maintained by HailBytes here.

Prowler
Prowler is a command-line tool for AWS that evaluates your infrastructure in comparison to standards set for AWS by the Center for Internet Security as well as GDPR and HIPAA inspections. You have the option of reviewing your complete infrastructure or a specific AWS profile or region. Prowler has the ability to execute many reviews at once and submit reports in formats including CSV, JSON, and HTML. Additionally, AWS Security Hub is included. Toni de la Fuente, an Amazon security expert who is still involved in the project’s maintenance, developed Prowler.
Security Monkey
In AWS, GCP, and OpenStack settings, Security Monkey is a watchdog tool that keeps an eye out for policy modifications and weak setups. For instance, Security Monkey in AWS notifies you whenever an S3 bucket as well as security group is created or removed, monitors your AWS Identity & Access Management keys, and does several other monitoring duties. Netflix created Security Monkey, albeit it only offers small issue fixes as of right now. AWS Config and Google Cloud Assets Inventory are vendor substitutes.
To see even more great open source tools on AWS, check out our HailBytes’ AWS marketplace offerings here.