
So, what is phishing?
Phishing is a form of social engineering that tricks people into revealing their passwords or valuable information. Phishing attacks can be in the form of emails, text messages, and phone calls.
Usually, these attacks pose as popular services and companies that people recognize easily.
When users click a phishing link in the body of an email, they are sent to a lookalike version of a site they trust. They are asked for their login credentials at this point in the phishing scam. Once they enter their information on the fake website, the attacker has what they need to access their real account.
Phishing attacks can result in stolen personal information, financial information, or health information. Once the attacker gets access to one account, they either sell the access to the account or use that information to hack other accounts of the victim.
Once the account is sold, someone who knows how to profit from the account will buy the account credentials from the dark web, and capitalize on the stolen data.
Here is a visualization to help you understand the steps in a phishing attack:

Phishing attacks come in different forms. Phishing can work from a phone call, text message, email, or social media message.
Generic Phishing
Generic phishing emails are the most common type of phishing attack. Attacks like these are common because they take the least amount of effort.
Hackers take a list of email addresses associated with Paypal or social media accounts and send a bulk email blast to the potential victims.
When the victim clicks the link in the email, it often takes them to a fake version of a popular website and asks them to log in with their account info. As soon as they submit their account info, the hacker has what they need to access their account.

Spear Phishing
Spear phishing is when an attacker targets a specific individual rather than sending a generic email to a group of people.
Spear phishing attacks try to specifically address the target and disguise themselves as a person the victim may know.
These attacks are easier for a scammer if you have personally identifiable information on the internet. The attacker is able to research you and your network to craft a message that is relevant and convincing.
Due to the high amount of personalization, spear phishing attacks are much harder to identify compared to regular phishing attacks.
They are also less common, because they take more time for criminals to pull them off successfully.
Whaling (CEO Fraud)
Compared to spear phishing attacks, whaling attacks are drastically more targeted.
Whaling attacks go after individuals in an organization such as the chief executive officer or chief financial officer of a company.
One of the most common goals of whaling attacks is to manipulate the victim into wiring large sums of money to the attacker.
Similar to regular phishing in that the attack is in the form of the email, whaling may use company logos and similar addresses to disguise themselves.
In some instances, the attacker will impersonate the CEO and use that persona to convince another employee to reveal financial data or transfer money to the attackers account.
Since employees are less likely to refuse a request from somebody higher up, these attacks are much more devious.
Attackers will often spend more time crafting a whaling attack because they tend to pay off better.

Angler Phishing
Angler Phishing is a relatively new type of phishing attack and exists on social media.
They do not follow the traditional email format of phishing attacks.
Instead, they disguise themselves as customer service representatives of companies and trick people into sending them information through direct messages.
A common scam is to send people to a fake customer support website that will download malware or in other words ransomware onto the victim’s device.

Vishing Attack
A vishing attack is when a scammer calls you to attempt to gather personal information from you.
Scammers usually pretend to be a reputable business or organization such as Microsoft, the IRS, or even your bank.
They use fear-tactics to get you to reveal important account data.This allows them to directly or indirectly access your important accounts.
Vishing attacks are tricky. Attackers can easily impersonate people that you trust.
Watch Hailbytes Founder David McHale talk about how robocalls will vanish with future technology.
Most phishing attacks occur through emails, but there are ways to identify their legitimacy.
When you open up an email check to see whether or not its from a public email domain (ie. @gmail.com).
If it is from a public email domain, it is most likely a phishing attack as organizations do not use public domains.
Rather, their domains would be unique to their business (ie. Google’s email domain is @google.com).
However, there are trickier phishing attacks that use a unique domain.
It’s useful to do a quick search of the company and check its legitimacy.
Phishing attacks always attempt to befriend you with a nice greeting or empathy.
For example, in my spam not too long ago I found a phishing email with the greeting of “Dear friend”.
I already knew this was a phishing email as in the subject line it said, “GOOD NEWS ABOUT YOUR FUNDS 21 /06/2020”.
Seeing those types of greetings should be instant red flags if you have never interacted with that contact.
The contents of a phishing email are very important, and you’ll see some distinctive features that make up most.
If the contents sound absurd, then most likely it’s a scam.
For example, if the subject line said, “You won the Lottery $1000000” and you have no recollection of participating then that’s a red flag.
When the content creates a sense of urgency like “it depends on you” and it leads to clicking a suspicious link then it is most likely a scam.
Phishing emails always have a suspicious link or file attached to them.
A good way to check if a link has a virus is to use VirusTotal, a website that checks files or links for malware.
Example of phishing email:
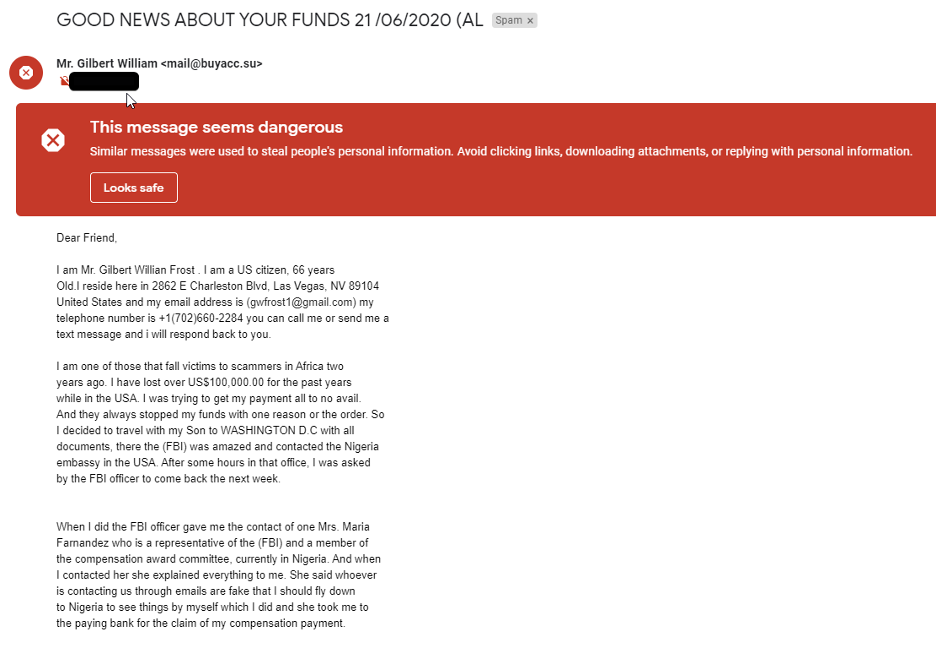
In the example, Google points out that the email can be potentially dangerous.
It recognizes that its content matches with other similar phishing emails.
If an email meets most of the criteria above, then it’s recommended to report it to reportphishing@apwg.org or phishing-report@us-cert.gov so that it gets blocked.
If you are using Gmail there is an option to report the email for phishing.
Even though phishing attacks are geared towards random users they often target employees of a company. However attackers are not always after a company’s money but its data.
In terms of business, data is far more valuable than money and it can severely impact a company. Attackers can use leaked data to influence the public by impacting consumer trust and tarnishing the company name.
But that’s not the only consequences that can result from that. Other consequences include negative impact on investor trust, disrupt business, and incite regulatory fines under the General Data Protection Regulation (GDPR).

Training your employees to deal with this problem is recommended to reduce successful phishing attacks.
Ways to train employees generally are to show them examples of phishing emails and the ways to spot them.
Another good way to show employees phishing is through simulation. Phishing simulations are basically fake attacks designed to help employees recognize phishing firsthand without any negative effects.
We will now share the steps you need to take to run a successful phishing campaign.
Phishing remains to be the top security threat according to WIPRO’s State of Cybersecurity Report 2020.
One of the best ways to collect data and educate employees is to run an internal phishing campaign.
It can be easy enough to create a phishing email with a phishing platform, but there is a lot more to it than hitting send. We will discuss how to handle phishing tests with internal communications.
Then, we will go over how you analyze and use the data that you collect.

Plan Your Communication Strategy
A phishing campaign isn’t about punishing people if they fall for a scam. A phishing simulation is about teaching employees how to respond to phishing emails. You want to make sure that you’re being transparent about doing phishing training in your company. Prioritize informing company leaders about your phishing campaign and describe the goals of the campaign.
After you send your first baseline phishing email test, you can make a company-wide announcement to all employees.
An important aspect of internal communications is to keep the message consistent. If you are doing your own phishing tests, then it’s a good idea to come up with a made up brand for your training material.

Coming up with a name for your program will help employees recognize your educational content in their inbox.
If you are using a managed phishing test service, then they will likely have this covered. Educational content should be produced ahead of time so that you can have an immediate follow-up after your campaign.
Give your employees instructions and information about your internal phishing email protocol after your baseline test.
You want to give your co-workers the opportunity to respond correctly to the training.
Seeing the number of people that correctly spot and report the email is important information to gain from the phishing test.
Understand How To Analyze Your Results
What should be your top priority for your campaign?
Engagement.
You can try to base your results on the number of successes and failures, but those numbers don’t necessarily help you with your purpose.
If you run a phishing test simulation and nobody clicks on the link, does that mean that your test was successful?
The short answer is “no”.
Having a 100% success rate doesn’t translate as a success.
It can mean that your phishing test was simply too easy to spot.
On the other hand, if you get a tremendous failure rate with your phishing test, it could mean something completely different.
It could mean that your employees aren’t able to spot phishing attacks yet.
When you get a high rate of clicks for your campaign, there is a good chance that you need to lower the difficulty of your phishing emails.
Take more time to train people at their current level.
You ultimately want to decrease the rate of phishing link clicks.
You may be wondering what a good or bad click rate is with a phishing simulation.
According to sans.org, your first phishing simulation may yield an average click rate of 25-30%.
That seems like a really high number.
Luckily, they reported that after 9-18 months of phishing training, the click rate for a phishing test was below 5%.
These numbers can help as a rough estimate of your desired results from phishing training.
Send A Baseline Phishing Test
To start your first phishing email simulation, make sure to whitelist the IP address of the testing tool.
This makes sure that employees will receive the email.
When crafting your first simulated phishing email don’t make it too easy or too hard.
You should also remember your audience.
If your coworkers are not heavy users of social media, then it probably wouldn’t be a good idea to use a fake LinkedIn password reset phishing email. The tester email has to have enough broad appeal that everyone in your company would have a reason to click.

Some examples of phishing emails with broad appeal could be:
Just remember the psychology of how the message will be taken by your audience before hitting send.
Continue with Monthly Emails
Continue to send phishing training emails to your employees. Make sure that you are slowly increasing the difficulty over time to increase people’s skill levels.
Frequency
It’s recommended to do monthly email sends. If you “phish” your organization too often, they are likely to catch on a little too quickly.
Catching your employees, a little bit off-guard is the best way to get more realistic results.

Variety
If you send the same type of “phishing” emails every time, you’re not going to teach your employees how to react to different scams.
You can try several different angles including:
As you send new campaigns, always make sure that you are fine tuning the relevance of the message to your audience.
Relevance
If you send a phishing email that isn’t related to something of interest, you may not get much of a response from your campaign.
After sending different campaigns to your employees, refresh some of the old campaigns that tricked people the first time and do a new spin on that campaign.
You’ll be able to tell the effectiveness of your training if you see that people are either learning and improving.
Follow The Data
From there you will be able to tell if they need more education on how to spot a certain type of phishing email.
There are 3 factors in determining whether you are going to create your own phishing training program or outsource the program.
Technical Expertise
If you are a security engineer or have one in your company, you can easily spawn up a phishing server using a pre-existing phishing platform to create your campaigns.
Experience
If you don’t have any security engineers, creating your own phishing program may be out of the question.
You may have a security engineer in your organization, but they may not be experienced with social engineering or phishing tests.
If you have someone that is experienced, then they would be reliable enough to create their own phishing program.
Time
This one is a really big factor for small to mid-sized companies.
If your team is small, it might not be convenient to add another task to your security team.
It is a lot more convenient to have another experienced team do the work for you.
How Do I Start?
You’ve gone through this whole guide to figure out how you can train your employees and you’re ready to start protecting your organization through phishing training.
What now?
If you are a security engineer and want to start running your first phishing campaigns now, go here to learn more about a phishing simulation tool that you can use to get started today.
Or…
If you are interested in learning about managed services to run phishing campaigns for you, learn more right here about how you can start your free trial of phishing training.

Use the checklist to identify unusual emails and if they are phishing then report them.
Even though there are phishing filters out there that can protect you, it’s not 100%.
Phishing emails are constantly evolving and are never the same.
To protect your company from phishing attacks you can partake in phishing simulations to decrease chances of successful phishing attacks.
We hope that you learned enough from this guide to figure out what you need to do next to decrease your chances of a phishing attack on your business.
Please leave a comment if you have any questions for us or if you want to share any of your knowledge or experience with phishing campaigns.
Don’t forget to share this guide and spread the word!
HailBytes
8 The Green
Suite A
Dover, DE 19901
Telephone: +1 (833) 892-3596
Email: Contact@HailBytes.com