Vulnerability Management as a Service: The Smart Way to Protect Your Organization

Vulnerability Management as a Service: The Smart Way to Protect Your Organization What is Vulnerability Management? With all the coding and software companies use, there’s always security vulnerabilities. There can be code at risk and a need to secure applications. That’s why we need to have vulnerability management. But, we already have so much on […]
Vulnerability Management as a Service: The Key to Compliance

Vulnerability Management as a Service: The Key to Compliance What is Vulnerability Management? With all the coding and software companies use, there’s always security vulnerabilities. There can be code at risk and a need to secure applications. That’s why we need to have vulnerability management. But, we already have so much on our plate to […]
How Vulnerability Management as a Service Can Help You Save Time and Money

How Vulnerability Management as a Service Can Help You Save Time and Money What is Vulnerability Management? With all the coding and software companies use, there’s always security vulnerabilities. There can be code at risk and a need to secure applications. That’s why we need to have vulnerability management. But, we already have so much […]
5 Benefits of Vulnerability Management as a Service
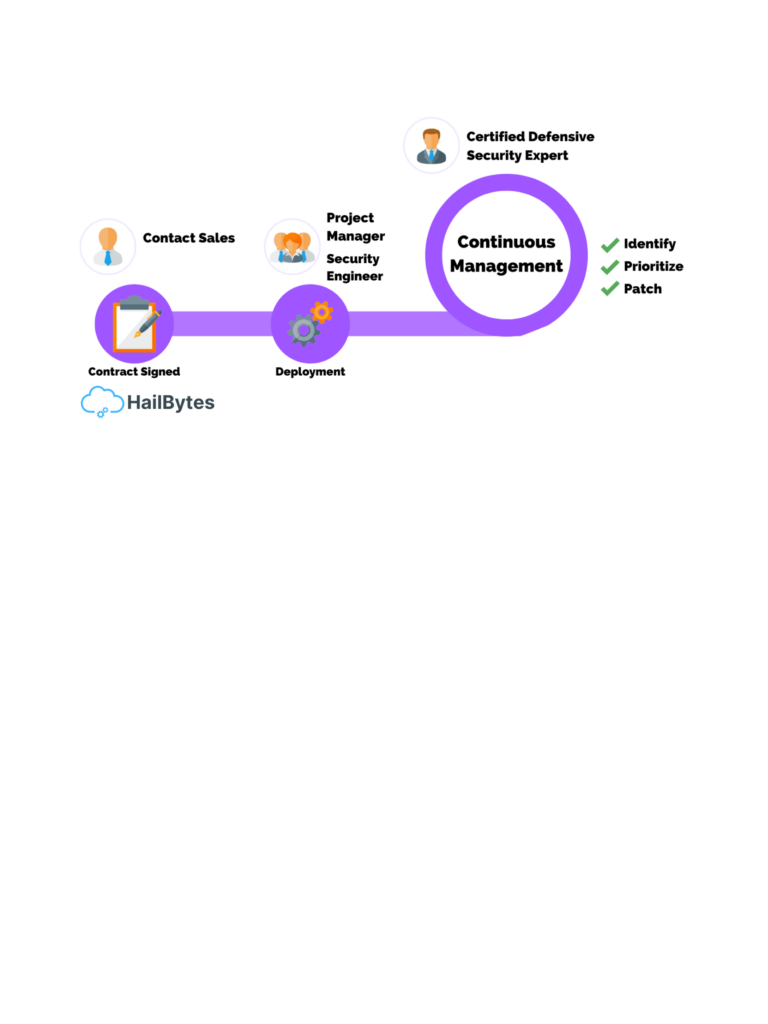
5 Benefits of Vulnerability Management as a Service What is Vulnerability Management? With all the coding and software companies use, there’s always security vulnerabilities. There can be code at risk and a need to secure applications. That’s why we need to have vulnerability management. But, we already have so much on our plate to worry […]
Best Practices for Building a Secure Network Infrastructure

Best Practices for Building a Secure Network Infrastructure Introduction A secure network infrastructure is the foundation of a robust cybersecurity strategy for any organization. By implementing best practices for building a secure network, businesses can effectively protect their sensitive data, systems, and resources from unauthorized access and cyber threats. Here are essential best practices to […]
What to Consider When Choosing a Third-Party Security Service Provider

What to Consider When Choosing a Third-Party Security Service Provider Introduction In today’s complex and ever-evolving cybersecurity landscape, many businesses turn to third-party security service providers to enhance their security posture. These providers offer specialized expertise, advanced technologies, and round-the-clock monitoring to protect businesses from cyber threats. However, choosing the right third-party security service provider […]


