5 Benefits of Vulnerability Management as a Service
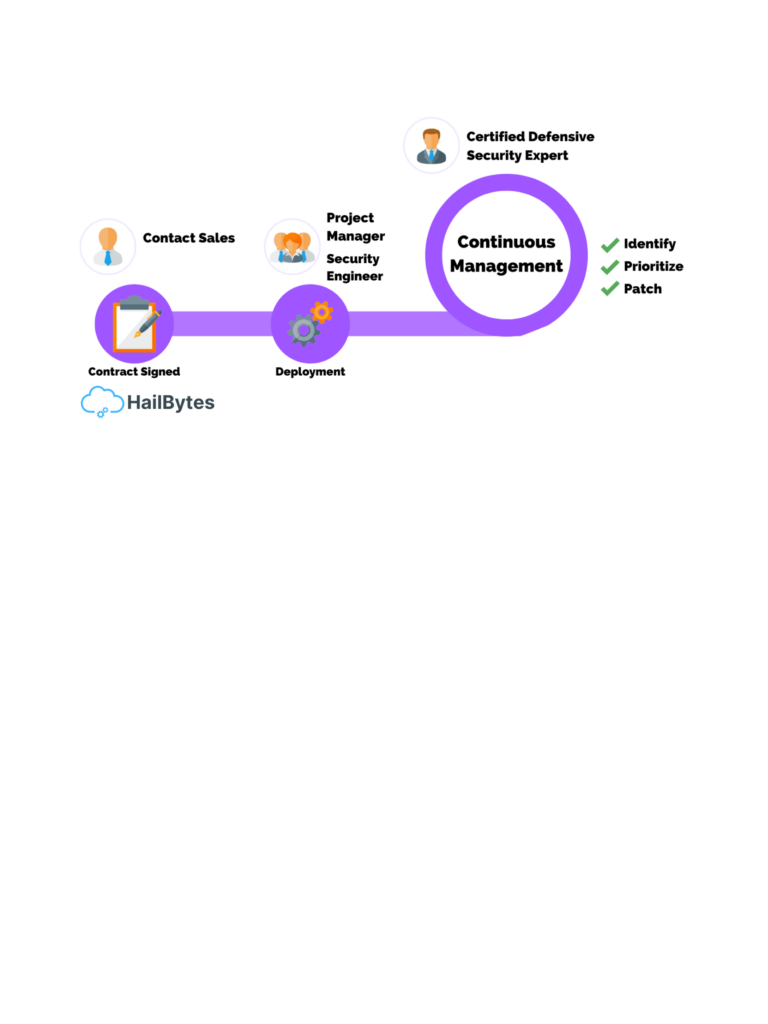
5 Benefits of Vulnerability Management as a Service What is Vulnerability Management? With all the coding and software companies use, there’s always security vulnerabilities. There can be code at risk and a need to secure applications. That’s why we need to have vulnerability management. But, we already have so much on our plate to worry […]
A Beginner’s Guide to Active Directory: Understanding Its Functionality and Benefits

A Beginner’s Guide to Active Directory: Understanding Its Functionality and Benefits Introduction Active Directory is a centralized and standardized system that stores and manages information about network resources, such as user accounts, computer accounts, and shared resources like printers. It’s a critical component of most enterprise-level networks, providing centralized management and security for network resources. […]
Social Network Security: Stay Safe with these 6 Quick Wins

Social Network Security: Stay Safe with these 6 Quick Wins Introduction Social networks have become an integral part of our daily lives, and while they offer many benefits, they also pose significant security risks. In this blog post, we will explore six quick wins for social network security that can help you stay safe while […]
Quick Cybersecurity Wins for Software Security

Quick Cybersecurity Wins for Software Security Introduction As technology advances, so does the threat landscape. Cybercriminals are continually looking for vulnerabilities in software to exploit, and this makes software security an essential aspect of cybersecurity. In this blog post, we will explore nine quick wins for software security that can help you defend against cyber […]
USB Drive Security: 7 Tips for Using Them Safely

USB Drive Security: 7 Tips for Using Them Safely Introduction USB drives are ubiquitous and useful, but they can also pose serious security risks. In this post, we’ll provide you with seven quick tips to help you use USB drives safely and securely. Scan USBs and Other External Devices for Viruses and Malware Before using […]
Debunking Some Common Cybersecurity Myths

Debunking Some Common Cybersecurity Myths Introduction Cybersecurity is a complex and constantly evolving field, and unfortunately, there are many myths and misconceptions about it that can lead to dangerous mistakes. In this post, we’ll take a closer look at some of the most common cybersecurity myths and debunk them one by one. Why it’s important […]

 reNgine Reconnaissance
reNgine Reconnaissance GoPhish Phishing Simulation
GoPhish Phishing Simulation  VPN Solutions
VPN Solutions ShadowSocks SOCKS5 Proxy
ShadowSocks SOCKS5 Proxy Vulnerability Calculator
Vulnerability Calculator  NEW
NEW Implementation Services
Implementation Services

 Documentation Hub
Documentation Hub Security Guides
Security Guides Free Security Tools
Free Security Tools Compliance Templates
Compliance Templates Training Videos
Training Videos Security FAQ
Security FAQ