How MFA-as-a-Service Can Improve Your Security Posture

How MFA-as-a-Service Can Improve Your Security Posture Introduction Have you ever been a victim of hacking? Financial loss, identity theft, data loss, reputationaldamage, and legal liability are all consequences that can result from this unforgiving attack.Equipping yourself with the necessary tools is how you can fight back and protect yourself andyour business. One such tool […]
How to Choose the Right MFA-as-a-Service Provider

How to Choose the Right MFA-as-a-Service Provider Introduction Have you ever experienced the frustration of being unable to access your password-protectedaccounts, only to discover that your data has been compromised or manipulated? Astechnology advances and becomes more accessible, the issue of password insecurity growsincreasingly significant. Ensuring the safety, stability, and success of your business ororganization […]
Email Security as a Service: The Future of Email Protection

Email Security as a Service: The Future of Email Protection Introduction Let me ask you a question: what do you think is the number one method of communication used by businesses, employees, students, etc.? The answer is email. You include it in most of your professional and academic documents when trying to communicate. It’s estimated […]
Web-Filtering-as-a-Service: A Secure and Cost-Effective Way to Protect Your Employees
Web-Filtering-as-a-Service: A Secure and Cost-Effective Way to Protect Your Employees What is Web-Filtering A Web filter is computer software that limits the websites a person can access on their computer. We use them to prohibit access to websites that host malware. These are usually sites associated to pornography or gambling. To put it simply, web […]
Tips and Tricks for Using Web-Filtering-as-a-Service
Tips and Tricks for Using Web-Filtering-as-a-Service What is Web-Filtering A Web filter is computer software that limits the websites a person can access on their computer. We use them to prohibit access to websites that host malware. These are usually sites associated to pornography or gambling. To put it simply, web filtering software filters out […]
How Web-Filtering-as-a-Service Works
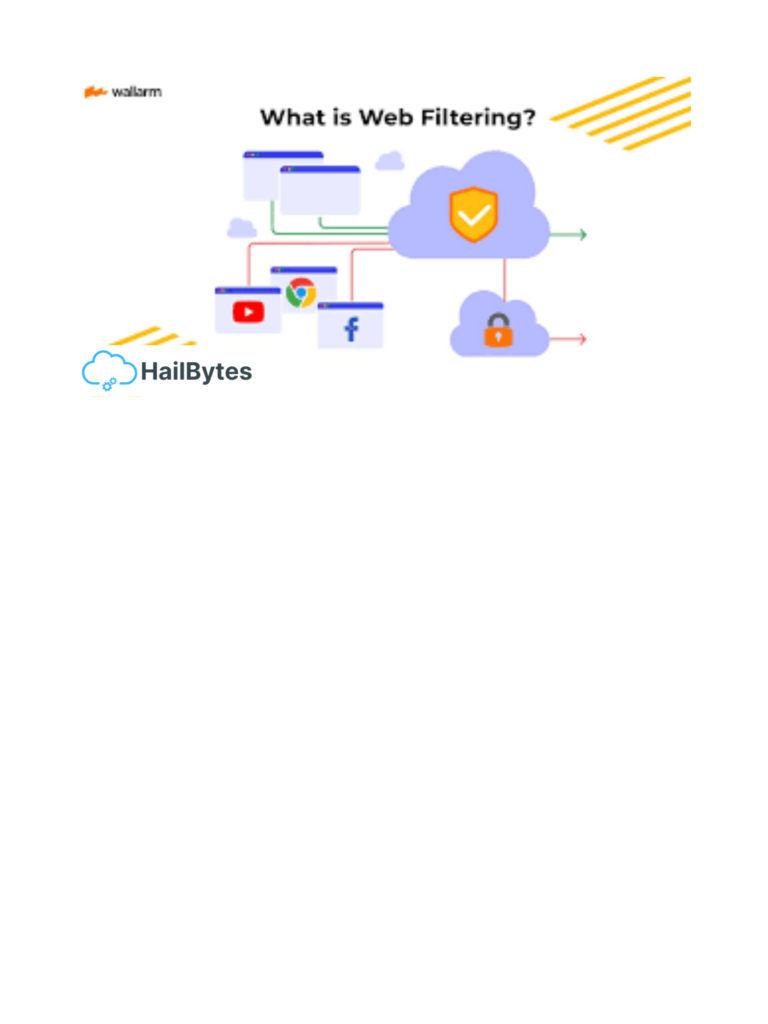
How Web-Filtering-as-a-Service Works What is Web-Filtering A Web filter is computer software that limits the websites a person can access on their computer. We use them to prohibit access to websites that host malware. These are usually sites associated to pornography or gambling. To put it simply, web filtering software filters out the web so […]


