Case Studies of How Web-Filtering-as-a-Service Has Helped Businesses
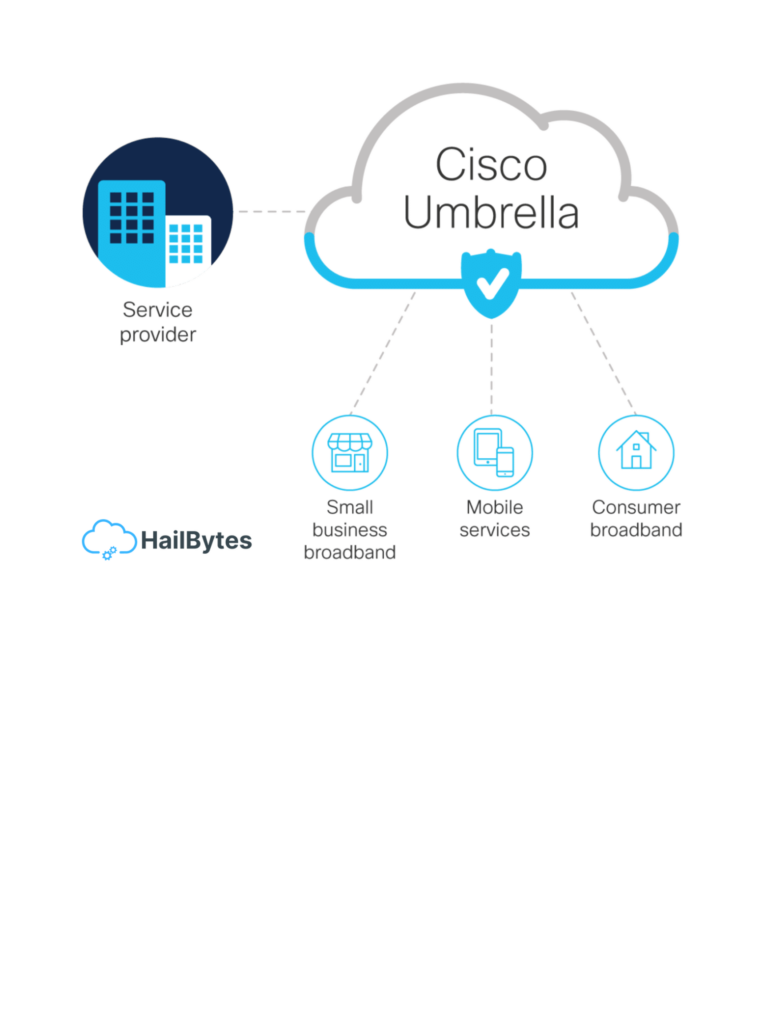
Case Studies of How Web-Filtering-as-a-Service Has Helped Businesses What is Web-Filtering A Web filter is computer software that limits the websites a person can access on their computer. We use them to prohibit access to websites that host malware. These are usually sites associated to pornography or gambling. To put it simply, web filtering software […]
Dark Web Monitoring-as-a-Service: Protect Your Organization from Data Breaches

Dark Web Monitoring-as-a-Service: Protect Your Organization from Data Breaches Introduction Businesses today are facing increasingly sophisticated attacks from cyber criminals and hackers. According to an IBM analysis report each data breach on average costs $3.92 million with almost half of all victims of data breaches being small businesses. On top of direct financial losses, your […]
Benefits of Using Dark Web Monitoring-as-a-Service

Benefits of Using Dark Web Monitoring-as-a-Service Introduction Businesses today are facing increasing attacks from cyber criminals and hackers. After accessing your network, a common place where they trade your sensitive information is the dark web. Unlike the traditional Internet, the dark web keeps Internet activity anonymous and private. On the dark web, sensitive information like […]
Benefits of Using Web-Filtering-as-a-Service
Benefits of Using Web-Filtering-as-a-Service What is Web-Filtering A Web filter is computer software that limits the websites a person can access on their computer. We use them to prohibit access to websites that host malware. These are usually sites associated to pornography or gambling. To put it simply, web filtering software filters out the web […]
Detecting and Preventing Supply Chain Attacks

Detecting and Preventing Supply Chain Attacks Introduction Supply chain attacks have become an increasingly common threat in recent years, and they have the potential to cause widespread harm to businesses and individuals alike. A supply chain attack occurs when a hacker infiltrates the systems or processes of a company’s suppliers, vendors, or partners, and uses […]
Social Network Security: Stay Safe with these 6 Quick Wins

Social Network Security: Stay Safe with these 6 Quick Wins Introduction Social networks have become an integral part of our daily lives, and while they offer many benefits, they also pose significant security risks. In this blog post, we will explore six quick wins for social network security that can help you stay safe while […]


