5 Benefits of Vulnerability Management as a Service
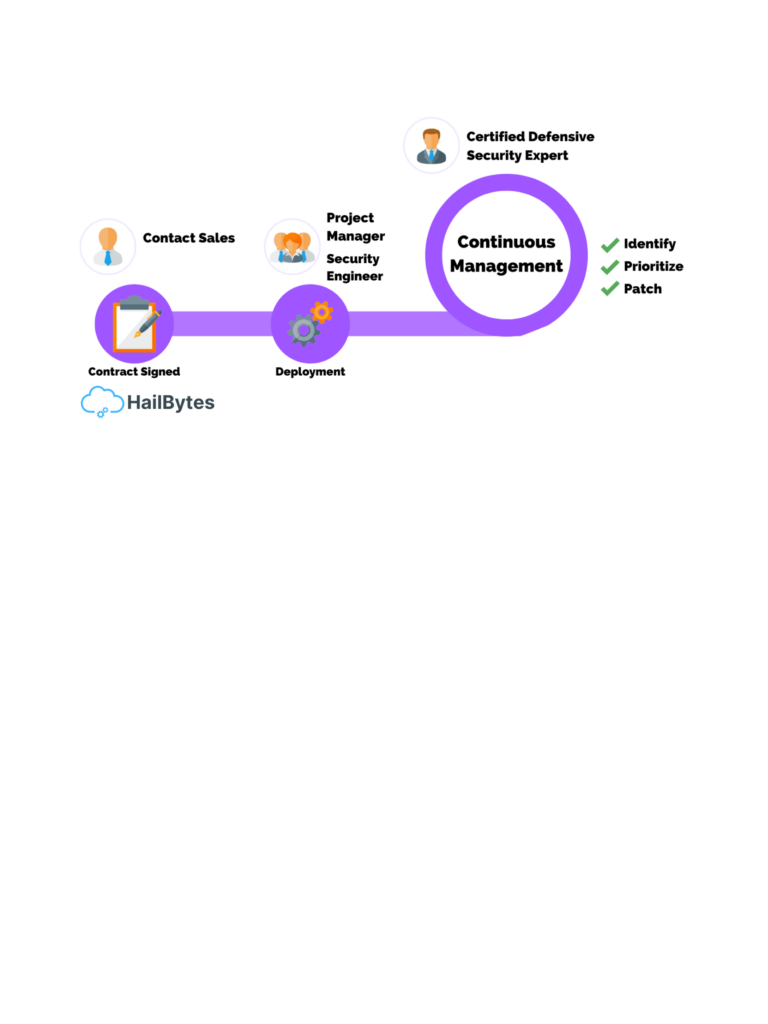
5 Benefits of Vulnerability Management as a Service What is Vulnerability Management? With all the coding and software companies use, there’s always security vulnerabilities. There can be code at risk and a need to secure applications. That’s why we need to have vulnerability management. But, we already have so much on our plate to worry […]
Training Employees to Recognize and Avoid Phishing Scams

Training Employees to Recognize and Avoid Phishing Scams Introduction In today’s digital age, where cyber threats continue to evolve, one of the most prevalent and damaging forms of attack is phishing scams. Phishing attempts can deceive even the most tech-savvy individuals, making it crucial for organizations to prioritize cybersecurity training for their employees. By equipping […]
Is stress bad for cybersecurity? More than you might think!

Is stress bad for cybersecurity? More than you might think! Introduction We all experience stress in our daily lives, whether it’s from work, relationships, or even just the news. However, did you know that stress can also have a significant impact on your cybersecurity career? In this post, we’ll talk about amygdala hijack and how […]
Top 7 Tips For Incident Response

Top 7 Tips For Incident Response Introduction Incident response is the process of identifying, responding to, and managing the aftermath of a cybersecurity incident. Here are the top 7 tips for effective incident response: Establish a clear incident response plan: Having a clear and well-documented incident response plan in place can help ensure that all […]
What Are The Stages Of Incident Response?

What Are The Stages Of Incident Response? Introduction Incident response is the process of identifying, responding to, and managing the aftermath of a cybersecurity incident. There are generally four stages of incident response: preparation, detection and analysis, containment and eradication, and post-incident activity. Preparation The preparation stage involves establishing an incident response plan and ensuring […]
What Is CMMC? | Cybersecurity Maturity Model Certification

What Is CMMC? | Cybersecurity Maturity Model Certification Introduction CMMC, or Cybersecurity Maturity Model Certification, is a framework developed by the Department of Defense (DoD) to assess and improve the cybersecurity practices of its contractors and other organizations that handle sensitive government data. The CMMC framework is designed to ensure that these organizations have sufficient […]

 reNgine Reconnaissance
reNgine Reconnaissance GoPhish Phishing Simulation
GoPhish Phishing Simulation  VPN Solutions
VPN Solutions ShadowSocks SOCKS5 Proxy
ShadowSocks SOCKS5 Proxy Vulnerability Calculator
Vulnerability Calculator  NEW
NEW Implementation Services
Implementation Services

 Documentation Hub
Documentation Hub Security Guides
Security Guides Free Security Tools
Free Security Tools Compliance Templates
Compliance Templates Training Videos
Training Videos Security FAQ
Security FAQ