5 Benefits of Vulnerability Management as a Service
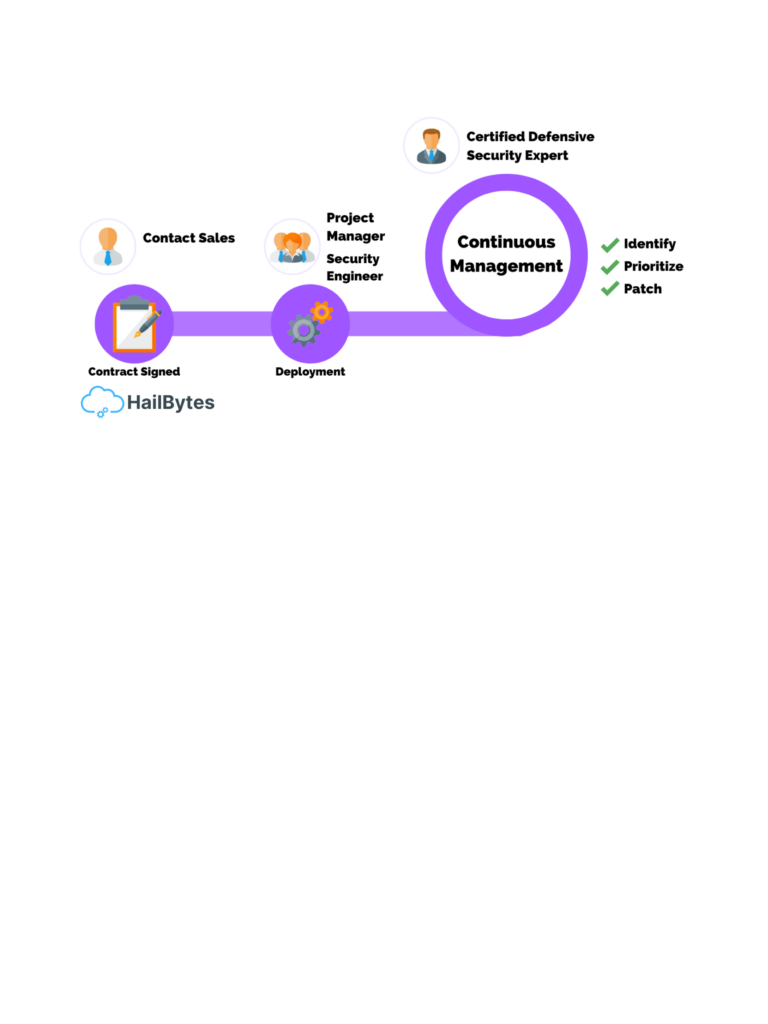
5 Benefits of Vulnerability Management as a Service What is Vulnerability Management? With all the coding and software companies use, there’s always security vulnerabilities. There can be code at risk and a need to secure applications. That’s why we need to have vulnerability management. But, we already have so much on our plate to worry […]
Shadowsocks vs. VPN: Comparing the Best Options for Secure Browsing

Shadowsocks vs. VPN: Comparing the Best Options for Secure Browsing Introduction In an era where privacy and online security are of paramount importance, individuals seeking secure browsing solutions often find themselves faced with a choice between Shadowsocks and VPNs. Both technologies offer encryption and anonymity, but they differ in their approach and functionality. In this […]
Training Employees to Recognize and Avoid Phishing Scams

Training Employees to Recognize and Avoid Phishing Scams Introduction In today’s digital age, where cyber threats continue to evolve, one of the most prevalent and damaging forms of attack is phishing scams. Phishing attempts can deceive even the most tech-savvy individuals, making it crucial for organizations to prioritize cybersecurity training for their employees. By equipping […]
The Benefits of Outsourcing IT Security Services

The Benefits of Outsourcing IT Security Services Introduction In today’s digital landscape, organizations face an ever-growing range of cyber threats that can compromise sensitive data, disrupt operations, and damage their reputation. As a result, ensuring robust IT security has become a top priority for businesses across various industries. While some companies choose to establish an […]
5 Common Mistakes That Make You Vulnerable to Phishing Attacks

5 Common Mistakes That Make You Vulnerable to Phishing Attacks Introduction Phishing attacks remain a prevalent cybersecurity threat, targeting individuals and organizations worldwide. Cybercriminals employ various tactics to deceive victims into revealing sensitive information or performing harmful actions. By avoiding common mistakes that make you vulnerable to phishing attacks, you can significantly enhance your online […]
Security Operations Budgeting: CapEx vs OpEx

Security Operations Budgeting: CapEx vs OpEx Introduction Regardless of business size, security is a non-negotiable necessity and should be accessible on all fronts. Before the popularity of the “as a service” cloud delivery model, businesses had to own their security infrastructure or lease them. A study conducted by IDC found that spending on security-related hardware, […]


