The principle of least privilege, also known as POLP, is a security principle that dictates that users of a system should be granted the least amount of privilege necessary to complete their tasks. This helps ensure that users can’t access or modify data they shouldn’t have access to.
In this blog post, we will discuss what the principle of least privilege is and how you can apply it in your business.
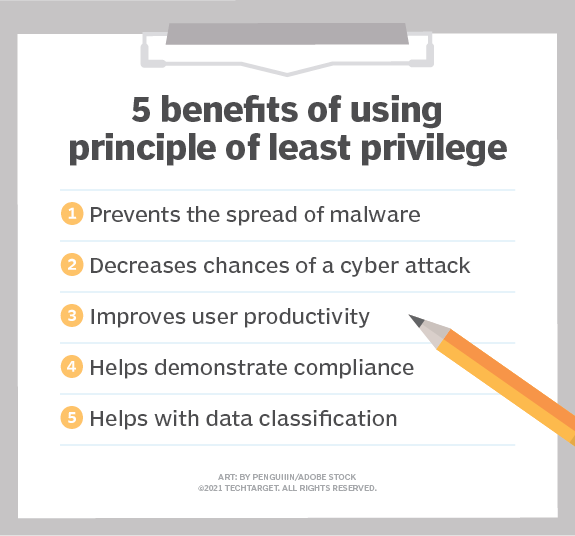
The principle of least privilege (POLP) is a security guideline that requires users be given only the minimal level of access necessary to perform their job duties.
Why do organizations use the principle of least privilege?
The purpose of POLP is to reduce potential damage from errors and malicious activity by limiting the privileges of users.
Applying the principle of least privilege can be difficult, as it requires careful thought about what each user needs to be able to do their job and nothing more.
There are two main types of privileges that need to be considered when applying the principle of least privilege:
– System privileges: These are privileges that allow users to perform actions on a system, such as accessing files or installing software.
– Data privileges: These are privileges that allow users to access and modify data, such as reading, writing, or deleting files.
System privileges are usually more restricted than data privileges, as they can be used to perform actions that could potentially harm the system. For example, a user with read access to a file can’t delete it, but a user with write access can. Data privileges should also be carefully considered, as granting users too much access can lead to data loss or corruption.
When applying the principle of least privilege, it’s important to strike a balance between security and usability. If privileges are too restrictive, users will be unable to do their jobs effectively. On the other hand, if privileges are too lax, there is a greater risk of security breaches. Finding the right balance can be difficult, but it’s essential to maintaining a secure system.
The principle of least privilege is an important security guideline that should be considered when designing any system. By carefully considering what each user needs to be able to do, you can help reduce the risk of data loss or damage from malicious activity.





