Phishing Awareness: How Does It Happen And How To Prevent It

Why Do Criminals Use A Phishing Attack?
What’s the biggest security vulnerability in an organization?
The people!
Whenever they want to infect a computer or gain access to important information like account numbers, passwords, or PIN numbers, all they have to do is ask.
Phishing attacks are commonplace because they are:
- Easy to do – A 6-year old child could perform a phishing attack.
- Scalable – They range from spear-phishing attacks that hit one person to attacks on an entire organization.
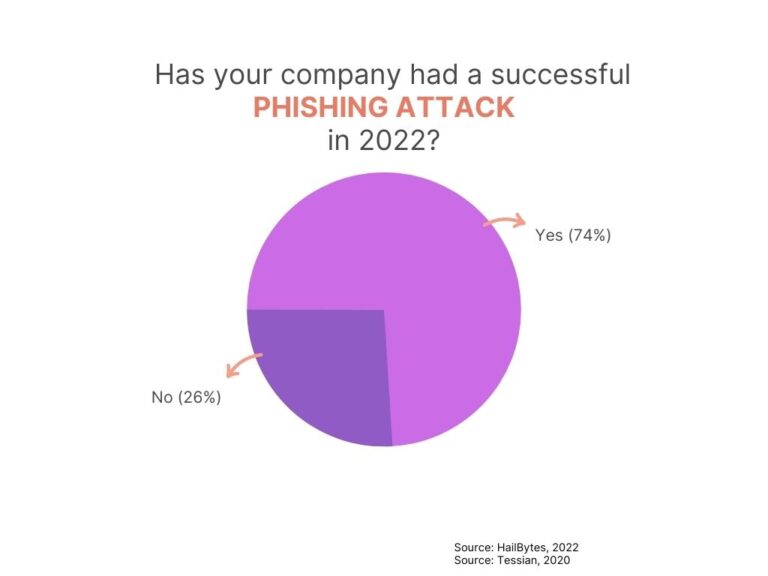
- Very effective – 74% of organizations have experienced a successful phishing attack.
Phishing attacks are not just popular because they are easy to accomplish successfully. They are popular because they are highly profitable. So, how do criminals profit from phishing scams? They typically sell your credentials on the dark web for other criminals to exploit. Here are some stats on what credentials go for on the dark web:
- Gmail account credentials – $80
- Credit card pin – $20
- Online bank credentials for accounts with at least $100 in them – $40
- Bank accounts with at least $2,000 – $120
You’re probably thinking, “Wow, my accounts are going for the bottom dollar!”
And this is true.
There are other types of accounts that go for a much higher price tag because they are easier to keep money transfers anonymous.
Accounts that hold crypto are the jackpot for phishing scammers.
The going rates for crypto accounts are:
- Coinbase – $610
- Blockchain.com – $310
- Binance – $410
There are also other non-financial reasons for phishing attacks.
Phishing attacks can be used by nation-states to hack into other countries and mine their data.
Attacks can be for personal vendettas or even to destroy the reputations of corporations or political enemies.
The reasons for phishing attacks are endless…
How Does A Phishing Attack Start?
A phishing attack usually starts with the criminal coming right out and messaging you.
They may give you a phone call, an email, an instant message, or an SMS.
They could claim to be someone who is working for a bank, another company you do business with, a government agency, or even pretending to be someone in your own organization.
A phishing email might ask you to click on a link or download and execute a file.
You may think it’s a legitimate message, click the link inside their message, and log in to what appears to be the website from the organization you trust.
At this point the phishing scam is complete.
You’ve handed over your private information to the attacker.
For more information on the current state of phishing you can check out our Ultimate Guide to Understanding Phishing in 2023 here:
The Ultimate Guide to Understanding Phishing in 2023
How To Prevent A Phishing Attack
The main strategy to avoid phishing attacks is to train employees and build organizational awareness.
Many phishing attacks look like legitimate emails and can pass through a spam filter or similar security filters.
At first glance, the message or the website might look real using a known logo layout, etc.
Luckily, detecting phishing attacks is not so difficult.
The first thing to look out for is the sender’s address.
If the sender address is a variation on a website domain that you may be used to, you may want to proceed with caution and not click anything in the email body.
You can also look at the website address where you’re redirected if there are any links.
To be safe, you should type the address of the organization you want to visit in the browser or use browser favorites.
Watch out for links that when hovered over shows a domain that is not the same as the company sending the email.
Read the content of the message carefully, and be skeptical of all messages asking you to submit your private data or verify information, fill out forms, or download and run files.
Also, don’t let the content of the message fool you.
Attackers often try to scare you to get you to click on a link or reward you to get your personal data.
During a pandemic or national emergency, phishing scammers will take advantage of people’s fears and use the content of the subject line or message body to scare you into taking action and clicking a link.
Also, check for bad spelling or grammar errors in the email message or website.
Another thing to keep in mind is that most trusted companies will not usually ask you to send sensitive data via web or mail.
That’s why you should never click on suspicious links or provide any sort of sensitive data.
What Do I Do If I Receive A Phishing Email?
If you receive a message that appears like a phishing attack, you have three options.
- Delete it.
- Verify the message content by contacting the organization through its traditional channel of communication.
- You can forward the message to your IT security department for further analysis.
Your company should already be screening and filtering the majority of suspicious emails, but anyone can become a victim.
Unfortunately, phishing scams are a growing threat on the internet and the bad guys are always developing new tactics to get through to your inbox.
Keep in mind that in the end, you’re the last and most important layer of defense against phishing attempts.
How To Stop A Phishing Attack Before It Happens
Since phishing attacks rely on human error to be effective, the best option is to train people in your business on how to avoid taking the bait.
This doesn’t mean that you have to have a big meeting or seminar on how to avoid a phishing attack.
There are better ways to find gaps in your security and improve your human response to phishing.
2 Steps You Can Take To Prevent A Phishing Scam
Step 1. Use A Phishing Simulator
https://www.youtube.com/watch?v=gJ5WNdpKCB8&t=16sA phishing simulator is software that allows you to simulate a phishing attack on all of the members of your organization.
Phishing simulators typically come with templates to help disguise the email as a trusted vendor or mimic internal email formats.
Phishing simulators don’t just create the email, but they help set up the fake website that the recipients will end up entering their credentials if they don’t pass the test.
Rather than scolding them for falling into a trap, the best way to handle the situation is to provide information on how to assess phishing emails in the future.
If someone fails a phishing test, it’s best to just send them a list of tips on spotting phishing emails.
You can even use this article as a reference for your employees.
Another major benefit of using a good phishing simulator is that you can measure the human threat in your organization, which is often hard to predict.
It can take up to a year and a half to train employees to a safe level of mitigation.
It’s important to choose the right phishing simulation infrastructure for your needs.
If you are doing phishing simulations across one business, then your task will be easier
If you are an MSP or MSSP, you may need to run phishing tests across multiple businesses and locations.
Opting for a cloud-based solution would be the best option for users running multiple campaigns.
At Hailbytes, we’ve configured GoPhish, one of the most popular open-source phishing Frameworks as an easy-to-use instance on AWS.
Many phishing simulators come in the traditional Saas model and have tight contracts associated with them, but GoPhish on AWS is a cloud-based service where you pay at a metered rate rather than a 1 or 2-year contract.
Step 2. Security Awareness Training
A key benefit of giving employees security awareness training is protecting them from identity theft, bank theft, and stolen business credentials.
Security awareness training is essential to improve employees’ ability to spot phishing attempts.
Courses can help train staff to detect phishing attempts, but only a few focus on small businesses.
It can be tempting for you as a small business owner to cut the costs of a course by sending some Youtube videos about security awareness…
but staff rarely remembers that type of training for more than a few days.
Hailbytes has a course that has a combination of quick videos and quizzes so you can track your employees’ progress, prove that security measures are in place, and massively cut your chances of suffering a phishing scam.
You can check out our course on Udemy here or click on the course below:
If you are interested in running a free phishing simulation to train your employees, head to AWS and check out GoPhish!
It’s easy to get started and you can always reach out to us if you need help getting set up.
