What is the CI/CD pipeline and what does it have to do with security?
In this blog post, we will answer that question and provide you with information on how to make sure your ci/cd pipeline is as secure as possible.
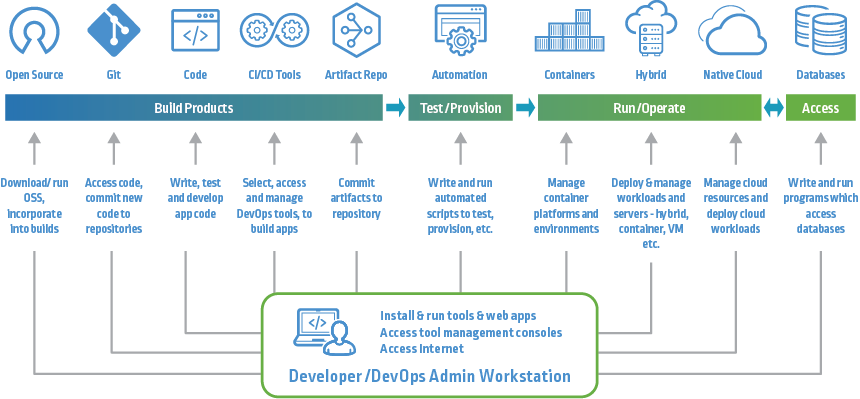
The CI/CD pipeline is a process that automates the build, test, and release of software. It can be used for both cloud-based and on-premises applications. Continuous integration (CI) refers to the automated process of integrating code changes into a shared repository several times a day.
This helps reduce the chances of conflicts between developers’ code changes. Continuous delivery (CD) takes things one step further by automatically deploying changes to a testing or production environment. This way, you can rapidly and safely deploy new features or bug fixes to your users.
One of the benefits of using a CI/CD pipeline is that it can help improve software quality and reduce risks. When code changes are automatically built, tested, and deployed, it’s easier to catch errors early on. This saves time and money in the long run since you won’t have to fix as many bugs later down the line. Additionally, automating deployments means that there’s less room for human error.
However, setting up a CI/CD pipeline does come with some security risks that you need to be aware of. For example, if an attacker gains access to your CI server, they could potentially manipulate your build process and inject malicious code into your software. This is why it’s important to have security measures in place to protect your CI/CD pipeline.
Some of the things you can do to secure your CI/CD pipeline include:
– Use a private git repository for your code changes. This way, only people who have access to the repository can view or make changes to the code.
– Set up two-factor authentication for your CI server. This adds an extra layer of security and makes it more difficult for attackers to gain access.
– Use a secure Continuous Integration tool that has built-in security features, such as encryption and user management.
By following these best practices, you can help keep your CI/CD pipeline secure and ensure that your software is of high quality. Do you have any other tips for securing a CI/CD pipeline? Let us know in the comments!
Do you want to learn more about CI/CD pipelines and how to set them up?
Stay tuned for more posts on DevOps best practices. If you’re looking for a Continuous Integration tool that has built-in security features, email us at contact@hailbytes.com for advance access to our secure Jenkins CI platform on AWS. Our platform includes encryption, user management, and role-based access control to help keep your data safe. Email for a free trial today. Thanks for reading, until next time.





