The Dark Side of Phishing: The Financial and Emotional Toll of Being a Victim

The Dark Side of Phishing: The Financial and Emotional Toll of Being a Victim Introduction Phishing attacks have become increasingly prevalent in our digital age, targeting individuals and organizations worldwide. While the focus is often on prevention and cybersecurity measures, it is essential to shed light on the darker consequences that victims face. Beyond the […]
Guarding the Cloud: A Comprehensive Guide to Security Best Practices in Azure

Guarding the Cloud: A Comprehensive Guide to Security Best Practices in Azure Introduction In today’s digital landscape, cloud computing has become an integral part of a business’s infrastructure. As businesses rely more on cloud platforms, ensuring good security practices is imperative. Among the leading cloud service providers, Microsoft Azure stands out for its advanced security […]
Web-Filtering-as-a-Service: A Secure and Cost-Effective Way to Protect Your Employees
Web-Filtering-as-a-Service: A Secure and Cost-Effective Way to Protect Your Employees What is Web-Filtering A Web filter is computer software that limits the websites a person can access on their computer. We use them to prohibit access to websites that host malware. These are usually sites associated to pornography or gambling. To put it simply, web […]
Tips and Tricks for Using Web-Filtering-as-a-Service
Tips and Tricks for Using Web-Filtering-as-a-Service What is Web-Filtering A Web filter is computer software that limits the websites a person can access on their computer. We use them to prohibit access to websites that host malware. These are usually sites associated to pornography or gambling. To put it simply, web filtering software filters out […]
How Web-Filtering-as-a-Service Works
How Web-Filtering-as-a-Service Works What is Web-Filtering A Web filter is computer software that limits the websites a person can access on their computer. We use them to prohibit access to websites that host malware. These are usually sites associated to pornography or gambling. To put it simply, web filtering software filters out the web so […]
Case Studies of How Web-Filtering-as-a-Service Has Helped Businesses
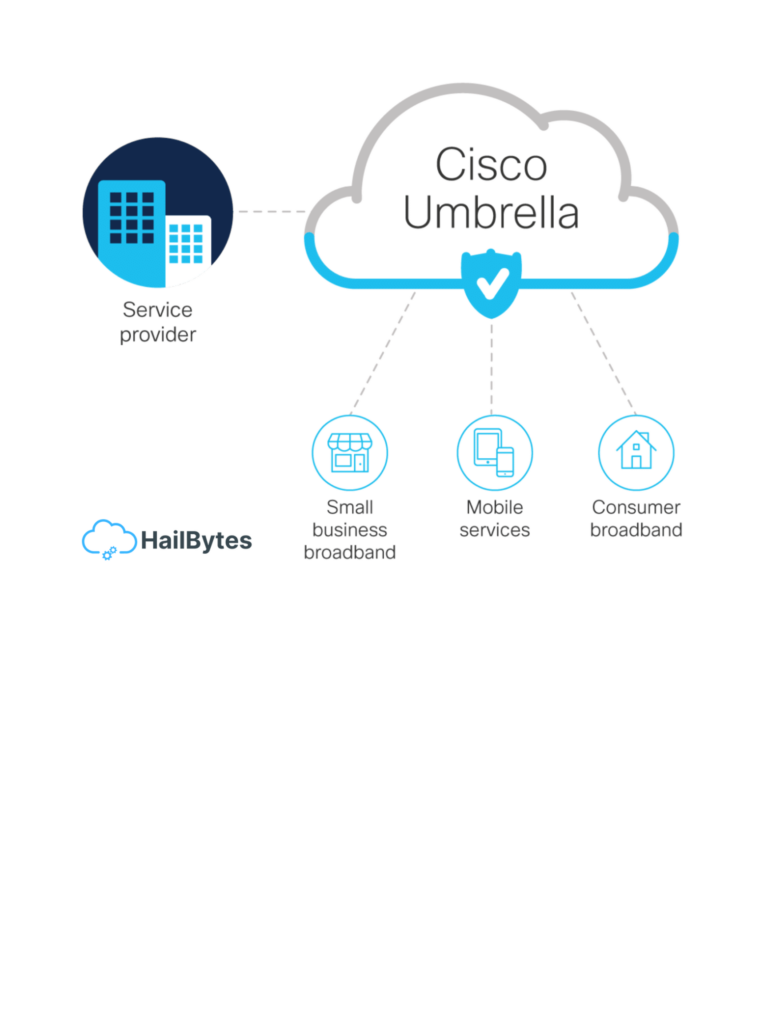
Case Studies of How Web-Filtering-as-a-Service Has Helped Businesses What is Web-Filtering A Web filter is computer software that limits the websites a person can access on their computer. We use them to prohibit access to websites that host malware. These are usually sites associated to pornography or gambling. To put it simply, web filtering software […]


